Information Security
Approach to Information Security
As the data-driven society advances and the importance of information security increases, we aim to achieve both data utilization and information security by promoting digital transformation and other measures. We are working with our suppliers to promote ongoing measures to protect the entire supply chain from the risk of cyberattacks that could target Tokyo Electron.
Main Activities

Information Security Systems
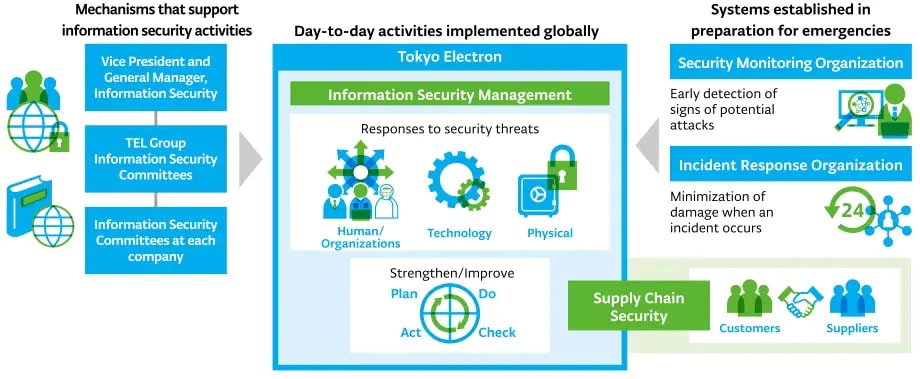
The Vice President and General Manager, Information Security, run the Security Committee and implement measures on a global scale. We hold the TEL Group Information Security Committee twice a year, and Information Security Committees at each company more than twice a year

Security at Manufacturing Sites and in Products
We implement security measures at each manufacturing site to ensure that the manufacturing systems that support our business activities are operating safely and stably while maintaining QCD*¹.
We are also working to ensure information security in our products as one of our services and as part of the quality that is required to meet our customers’ expectations.
QCD: Quality, Cost, Delivery

Information Security Management
We regularly verify and revise our global information security regulations, and continuously conduct information security education and phishing email training for all executives and employees. We also hold seminars for management twice a year to share the latest situation on information security, including cyber security. In addition, we implement risk assessments and internal audits for each department of the entire Company, evaluate risks and undertake improvement activities for technological, human, organizational and physical security measures.

Supply Chain Security
We respond to customer requests for security and work with our suppliers to visualize, evaluate and improve their security situations, to ensure that confidential information and information on our customers and suppliers that is shared in the course of business activities can be used safely without a loss of convenience.

Responses to Security Threats
We have proactively introduced advanced technology and established a dedicated security organization, and are operating a robust monitoring system, to respond to security threats such as cyberattacks (including ransomware) and information leaks.

Increasing Resilience
We operate a system that can detect the occurrence of security incidents, and have structures in place that aim to respond to issues and recover systems swiftly. We also carry out incident response training for the entire Company, including management, and confirm pre-determined procedures to ensure that impacts on operations and on customers will be minimized even in the event of operations being disrupted by an incident. We also implement a penetration test* for systems-related aspects twice a year and are developing improvement activities on an ongoing basis.
Penetration test: A test method for verifying vulnerabilities in networks, PCs, servers and systems.
Overview of Information Security